Blesta 5.6 Beta Released
We are pleased to announce that Blesta 5.6.0 BETA 1 has been released!
Can I participate in the beta?
If you have an owned or monthly license with us directly, you may download blesta-5.6.0-b1.zip in the client area now (Login Required). If you obtained your license from a reseller or distributor, you may be able to participate. Contact your reseller to find out. As with any beta, this release is for non-production use only and is unsupported. DO NOT UPGRADE YOUR PRODUCTION. During installation, choose to start a free trial, open a ticket to request a trial key, or use your dev license if you have one.
Once you are up and running, head to the forums to report any issues and let us know what you think! If you have a license and are verified or become verified on our Discord chat, you’ll have access to a license holder only beta forum.
Visit the Beta Forums! Visit Discord Chat!
So what is new in 5.6?
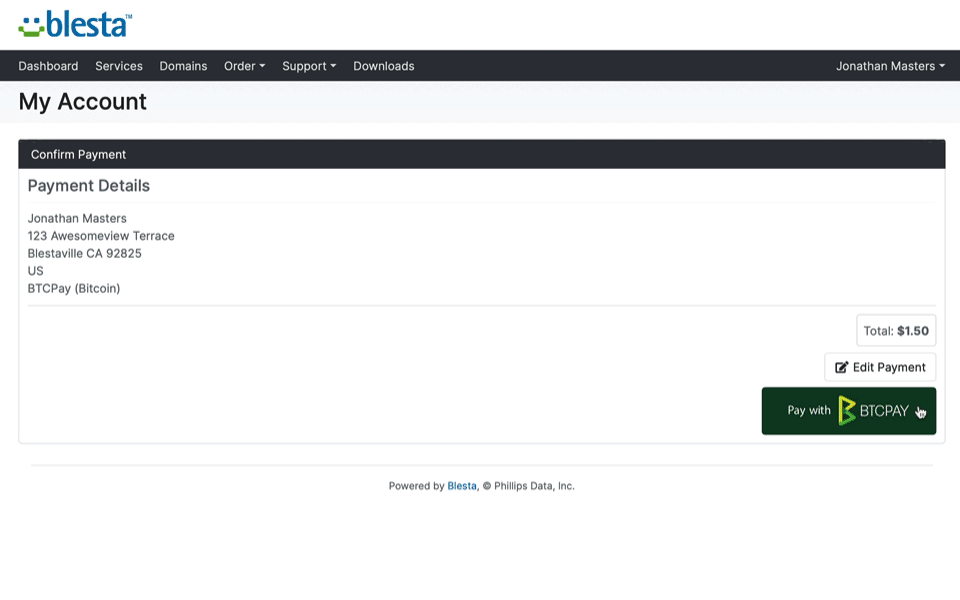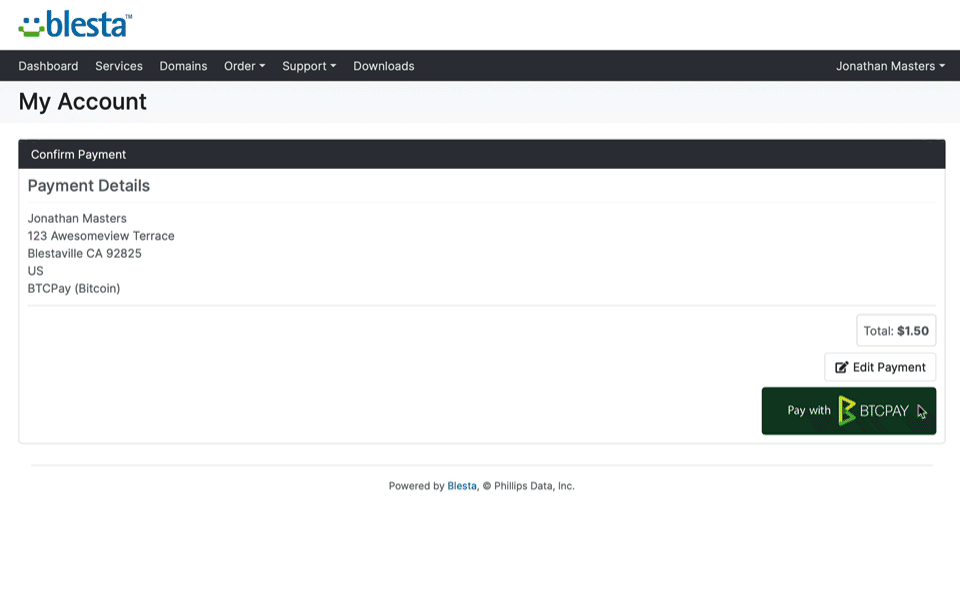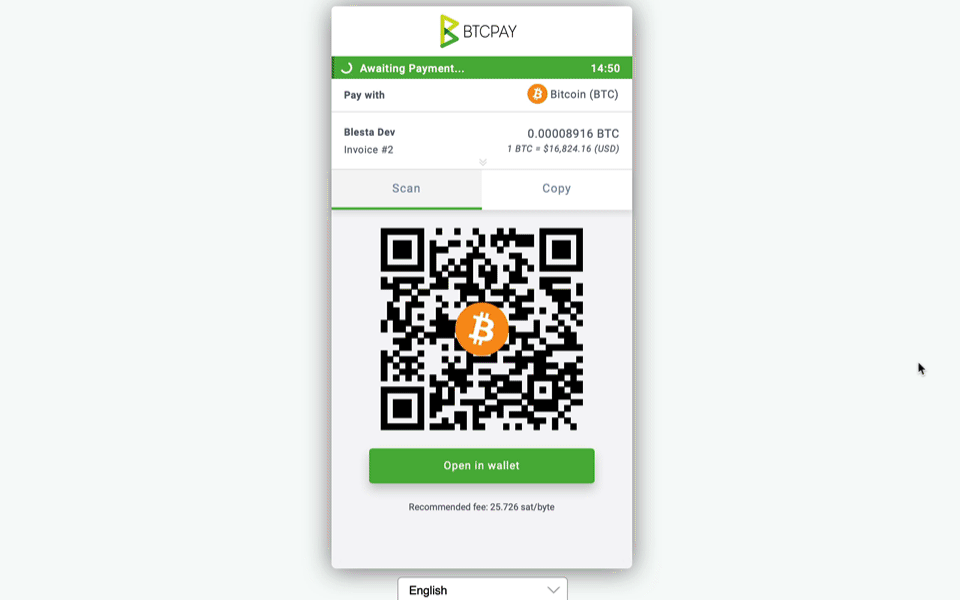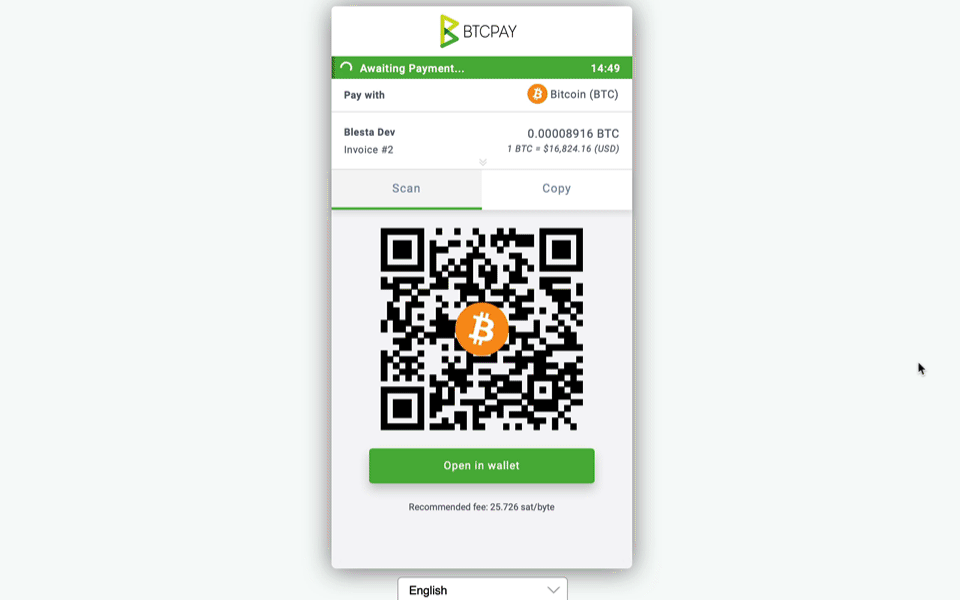
Blesta version 5.6 includes a new highly requested OVH Domains registrar module and an improved domain import process when migrating from the competition. Domains are imported more reliably, and domains that were using an unsupported registrar are now imported with the Generic Domains module instead of the Universal module. We also added the payment gateways BTCPayServer and Payfast. We added stable download URLs to the Download Manager, Staff only KB articles to the Support Manager, and more.
New and Updated Extensions
- OVH Domain Registrar module has been added.
- BTCPayServer payment gateway has been added.
- Payfast payment gateway has been added.
- Support Manager now includes a client dashboard widget (Can be disabled or sorted like all client widgets).
- Support Manager now supports Staff only Knowledgebase Articles.
- Domain Manager now includes a config option description for TLD features.
- Import Manager has been updated to include better support for importing domains from WHMCS.
- Import Manager now includes a mapping file to import SolusVM services from WHMCS using the module.
- Download Manager now supports stable download URLs (think latest.zip).
- cPanel module now makes use of the password generator.
- Pterodactyl module now allows for unlimited swap, and the panel port can be specified within the module.
- Stripe Payments gateway has been improved, particularly as it relates to handling errors.
- Order plugin was updated to add a show cart button for “domain and other” order form types for all cases.
Changes to the Core
- PHP 8.1 is now supported with Ioncube, and we continue to ship a hotfix-php8 directory for SourceGuardian for PHP 8.0/8.1.
- It’s now possible to update the email templates from email and from name fields in bulk.
- Package edit validation was updated to prevent changing term, period, or currency for in-use pricing.
Notes for Developers
- Added the ability for registrar modules to validate registration and transfer terms for TLDs.
- If you haven’t already, we recommend updating your extensions to work with PHP 8.0/8.1.
Client Template Changes
- /app/views/client/bootstrap/client_accounts_contact_info.pdt new
- /app/views/client/bootstrap/client_contacts_phone_numbers.pdt updated
- /app/views/client/bootstrap/partial_fields.pdt updated
Staff Template Changes
- /app/views/admin/default/admin_company_emails_templates.pdt updated
- /app/views/admin/default/admin_company_groups_add.pdt updated
- /app/views/admin/default/admin_company_groups_edit.pdt updated
- /app/views/admin/default/admin_company_require_fields_form.pdt updated
See the release notes for more details on this release.
Note Regarding PHP 8
We recommend exercising caution when using PHP 8 for production use. Many 3rd party or custom extensions may not yet be compatible with PHP 8. If upgrading Blesta, it is best to use a PHP version that is compatible with both the release you are upgrading from and the release you are upgrading to.
Blesta supports PHP 7.2, 7.3, 7.4, 8.1 through Ioncube using the default files, and PHP 8.0/8.1 through SourceGuardian via the hotfix-php8 directory. Report any PHP 8 related issues for Blesta or official extensions on our forums or Discord #beta channel.
Is there something you want to see in Blesta? Create a new feature request or upvote an existing one!
When is the final release?
Version 5.6 will be officially released after the beta phase has completed, which we expect to happen soon. Once we deem 5.6 stable for production, a final release will be issued. You can help speed things along by participating in the beta!
Blesta 5.5.3 Patch Released
We are pleased to announce the released of Blesta 5.5.3, which addresses bugs discovered in the 5.5 branch. A big thanks to everyone who participated in helping to make Blesta better by reporting and confirming bugs on our forums and discord chat, we appreciate your help!
The release notes are available at https://docs.blesta.com/display/support/5.5.3.
Always run /admin/upgrade in your browser or via CLI after updating the files for your installation. Patch releases may only be applied to the minor release to which it belongs. Only apply this patch if you are running 5.5.0, 5.5.1, or 5.5.2. If you are running an earlier version, you must download the full release.
Download 5.5.3 Patch Download 5.5.3 Full
SHA256 Sum
% blesta-5.5.3.zip
436a6a843109d3b43f7d1ed49f58dbd9be2471f35438c5ccf014a8a5467c000b
% blesta-5.5.0-5.5.3.zip
8c5a5943921acb71c75ac7d96c44b79122bb6a5dd313c2749da79f727e913e05
To patch your installation, please follow the instructions for Patching an Existing Install from our user manual.
Related Tags:
Blesta 5.5.2 Patch Released
We are pleased to announce the released of Blesta 5.5.2, which addresses bugs discovered in the 5.5 branch. A big thanks to everyone who participated in helping to make Blesta better by reporting and confirming bugs on our forums and discord chat, we appreciate your help!
The release notes are available at https://docs.blesta.com/display/support/5.5.2.
Always run /admin/upgrade in your browser or via CLI after updating the files for your installation. Patch releases may only be applied to the minor release to which it belongs. Only apply this patch if you are running 5.5.0, or 5.5.1. If you are running an earlier version, you must download the full release.
Download 5.5.2 Patch Download 5.5.2 Full
SHA256 Sum
% blesta-5.5.2.zip
d7972fc92edb0ef09b709df6481f54d8df3b402649506cb6194bce560c47d1ae
% blesta-5.5.0-5.5.2.zip
c46618c0a3284b4197e7912d9f0649573790043d2f0b610689af79397e8b266e
To patch your installation, please follow the instructions for Patching an Existing Install from our user manual.
Related Tags:
Blesta 5.5.1 Patch Released
We are pleased to announce the released of Blesta 5.5.1, which addresses bugs discovered in the 5.5 branch. A big thanks to everyone who participated in helping to make Blesta better by reporting and confirming bugs on our forums and discord chat, we appreciate your help!
The release notes are available at https://docs.blesta.com/display/support/5.5.1.
Always run /admin/upgrade in your browser or via CLI after updating the files for your installation. Patch releases may only be applied to the minor release to which it belongs. Only apply this patch if you are running 5.5.0. If you are running an earlier version, you must download the full release.
Download 5.5.1 Patch Download 5.5.1 Full
SHA256 Sum
% blesta-5.5.1.zip
84018a26e7539429061440565b7db09ec6c1b3f8c19db293d7b8ac3f360517ba
% blesta-5.5.0-5.5.1.zip
f3b8e65b1f67a4cd8f00f3ca412a31c3c4fad0b5ba016b5fd1bde0816d656627
To patch your installation, please follow the instructions for Patching an Existing Install from our user manual.
Related Tags:
Blesta 5.5 Released
Blesta 5.5 is now available! The domain manager continues to get updates, including a bulk TLD import with pricing markup, advanced renewal of domains, and automatic price overrides for domains, and a new internet.bs registrar module. We also added an abandoned order feature, an option to hide client fields that are not required on both order forms and within the client area, adjust the start value and format of client ID’s, and more.
Download 5.5SHA256 Sum
77895977ba9054536bf7d945059f64011413b397d1ab914f163845fceb6624bb
If upgrading from a release prior to 5.0, please review the version 5.0 announcement prior to upgrading. 5.0 was a major release and increased system requirements. ALWAYS BACKUP YOUR FILES + DATABASE PRIOR TO UPGRADING.
See the documentation for details on how to install or upgrade.
What’s new in 5.5?
- Added a bulk TLD import option to the domain manager.
- Added the option for domains to renew further in advance than services.
- Added an option to lock in prices for new domains.
- Added new filter options to the Domain Manager, to filter by TLD or Registrar.
- Added a new Internet.bs domain registrar module.
- Added a new abandoned order option to send reminders to clients with unpaid orders.
- Added an option to hide client fields that are not required on orde forms and within the client area.
- Added the ability to set the Client ID Start Value, Client ID Format, and Client ID Increment value.
- Added a Package setting to automatically set a price override for new services, locking in the original price.
- Added transaction messages within the transaction expand area for supported gateways.
- Updated the Portal plugin to add support for multi-language.
- Updated Stripe Payments to show an ACH “Mandate”, and add support for transaction messages.
- Updated Namecheap, Namesilo, and Logicboxes to support TLD import and price sync.
See our beta announcement for more and the release notes for everything.
Developers
Reminder: If you are a developer, you should review the version 5 Migration Guide and update your extensions if you haven’t already done so.
- Added a new event for Email Verification.
- Added a Doc Comments file in ~/lib/doc_comments.php for auto completion support in IDEs.
- Modules may now insert their own content in the client service management overview page.
- We recommend updating your extensions to support PHP 8 if they don’t already.
Sponsored Development
Sponsored development is a good way to support Blesta and get a shout out for your company! Interested? Reach out and say hello.
Stay Connected!
Like our Facebook page, join our Facebook group and Subreddit, follow us on Twitter, and join us in Discord.
