
Abdy
-
Posts
407 -
Joined
-
Last visited
-
Days Won
36
Posts posted by Abdy
-
-
The included WHMCS importer with Blesta can import the services too, but the services will be assigned to the core cPanel module.
-
1 hour ago, agentmishra said:
hello every one
when i try to signup and create a user, i get this error
Invalid client group ID.
Invalid client ID.
if i may get help?
I guess that it's a problem with Blesta and not the module, Uninstall the module and try again and check if the error persist.
-
13 minutes ago, Lucas said:
I don't know if it's a good idea or not, but maybe you could do an open fund with the approximate costs you consider to have in development and those interested can help out.
Another option that I have in mind, it's a crowdfunding campaign.
-
40 minutes ago, Lucas said:
Would love an update for this.
Me too.

Soon I will open a thread to find if someone is interested in sponsoring the module, And bring the module back to life. :)
-
If you have problems with BlestaCMS, update the plugin to the latest version (1.2.3) and then go to the file /controllers/main.php and find the line:
} elseif (isset(CURRENTLANGUAGE) && (null !== CURRENTLANGUAGE) && $this->CmsPages->langExists(CURRENTLANGUAGE)) {
and replace it with
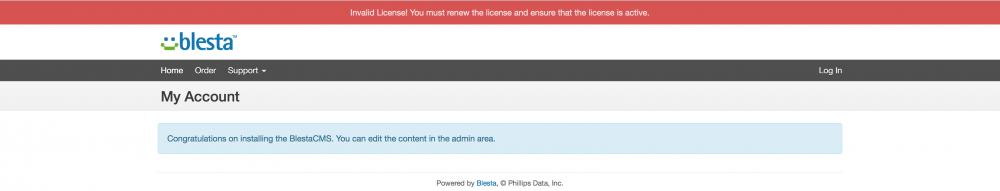
} elseif (defined('CURRENTLANGUAGE') && $this->CmsPages->langExists(CURRENTLANGUAGE)) {This will fix the blank page or empty page error (like the @timnboys screenshot).
-
2 hours ago, timnboys said:
great that is just what I need today

I tested the Blesta CMS code and the license verification are working fine. You have the latest version of the plugin installed? Enable the Error reporting and check if the plugin throw an error.
-
-
5 minutes ago, timnboys said:
I sent a email yesterday to mike, but without response.

Sorry, but I can't do nothing about the Blesta CMS plugin, due Licensecart hold all the rights over the plugin and all changes needs his approval, but is strange that not works.
-
Sorry for the delay, I paused the development at the moment, because I'm busy doing other projects.

-
Hi,
I guess that Blesta Addons has already a OVH Module, try to search in the forum. If not, You can send me a PM with the API documentation and I can give you a free quote.
Best Regards.
-
-
-
If you are interested I have a Blockhain Gateway, You can send me a PM and I will send you a free quote.

-
56 minutes ago, timnboys said:
I am glad you found out CentOS 6 is better than Debian 9 lol
Thanks, CentOS it's much better than Debian IMHO. I will make a last update, When I connect my computer to the VPN I can't access the Server, I can access the server only from the Internet but not inside the VPN, So I added this additional rules: I hope this thread some day can help other people with a similar problem.
iptables -t nat -A POSTROUTING -s z.z.z.z -j SNAT --to-source y.y.y.y iptables -t nat -A PREROUTING -d y.y.y.y -j DNAT --to-destination z.z.z.z iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE -
I finally found a solution, I re-installed the VPS with CentOS 6 (originally I deployed Debian 9) and I used the following rules:
Quoteiptables -t nat -A POSTROUTING -o eth0 -s z.z.z.z -j SNAT --to-source y.y.y.y
iptables -t nat -A PREROUTING -i eth0 -d y.y.y.y -j DNAT --to-destination z.z.z.z
iptables -A FORWARD -s y.y.y.y -j ACCEPT
iptables -A FORWARD -d z.z.z.z -j ACCEPTNow, I can access my server from the internet.

- Paul, Michael and Blesta Addons
-
 3
3
-
Thanks, I will give a try. All my servers are colocated in Datacenters, but this server is only for my own use, for fun and testing.
EDIT: Unfortunately doesn't work, because the link is intended for OpenVPN users. I'm using L2TP/IPSec. Thanks anyway.
-
Hi,
I decided this week wire my house and build a home network, As part of my home network, I purchased an old Xserve from 2009 and I installed macOS Sierra, But the problems start when I try to access the server outside of my network, I forwarded the ports on my Router but I found another problem, My router is inside a big NAT from my ISP. (I stole a diagram from ServerFault that shows my situation)

So I thought in two possible solutions:
- Get a Dedicated IP from my ISP
- Use a VPN
First of all, I called to my ISP asking for a dedicated IP address, unfortunately they only offer dedicated IP in business plans (that are kinda expensive), so it's not an option for me.
So I decided to go with the second option, use a VPN. I purchased a small VPS with two dedicated IP address (x.x.x.x and y.y.y.y) from a very know cloud provider, and then I proceed to install xl2tpd with IPsec in the VPS.
Installing XL2TPD with IPsec in CentOS 6
Searching on Google, I found very easy-to-use installation script, that you can find on GitHub here: https://github.com/hwdsl2/setup-ipsec-vpn
It's very recommendable first of all update the OS dependencies execution "yum update", and then install IPsec. You can do all this in one step:
yum -y update && wget https://git.io/vpnsetup-centos -O vpnsetup.sh && sudo sh vpnsetup.sh && chkconfig ipsec onAnd that's been all, You will see in the terminal at the end of the installation your VPN access details, Save this in a secure place.
Enabling IP Forwarding
After the installation I tested the VPN on my computer and my Android Phone, and the navigation works pretty well. So in order to get access to my server from the Internet, I configured the VPN on the server, You can find here a detailed explanation how to configure your new VPN in your OS: https://github.com/hwdsl2/setup-ipsec-vpn/blob/master/docs/clients.md
Now when your server is connected to the VPN, we need to check what is the Local IP assigned by the VPN to our server, For explanation purposes I will use the IP z.z.z.z, The installation script by default adds a DROP policy to the Iptables firewall, so first we need to remove them.
First we must activate the IP forwarding, to activate it you must modify the following parameters as shown below
net.ipv4.ip_forward = 1 net.ipv6.conf.all.accept_ra=2 net.ipv6.conf.eth0.accept_ra=2These parameters must be modified, or if they do not exist add them at the end, in the file
/etc/sysctl.confNow we will save all the Iptables rules in a file called "rules.v4"
mkdir /etc/iptables/ iptables-save > /etc/iptables/rules.v4Then open the new file with vi or nano.
nano /etc/iptables/rules.v4Now you need to find those lines in the file and remove them and save the file:
-A FORWARD -j REJECT --reject-with icmp-host-prohibited -A INPUT -j REJECT --reject-with icmp-host-prohibitedAfter save the file you need to restore them to Iptables, to update the new rules:
iptables -F iptables-restore < /etc/iptables/rules.v4 service iptables save service iptables reloadNow the final step, you need enable IP Forwarding at the OS level:
echo "1" > /proc/sys/net/ipv4/ip_forward && sysctl net.ipv4.ip_forward=1Now, reboot your VPS.
Forward Local IP
Now to access your server from the Internet, we need forward the Local IP (z.z.z.z) to the Public IP, I will forward the server to the y.y.y.y IP.
This step is easy, we only need add some rules to Iptables, this rules will forward all the ports to the local IP.
iptables -t nat -A POSTROUTING -o eth0 -s z.z.z.z -j SNAT --to-source y.y.y.y iptables -t nat -A PREROUTING -i eth0 -d y.y.y.y -j DNAT --to-destination z.z.z.z iptables -A FORWARD -s y.y.y.y -j ACCEPT iptables -A FORWARD -d z.z.z.z -j ACCEPT service iptables save service iptables reloadAnd that is all! Now you can access your amazing server from http://y.y.y.y/

- Blesta Addons and Paul
-
 1
1
-
 1
1
-
Stripe? Braintree?
-
Twig is another option. https://twig.symfony.com
-
-
-
Hi,
You can send me a PM with more details about your project and I can send you a free quote.

Best Regards.
-
Probably I will publish a private beta soon.
- Michael, Blesta Addons and evolvewh
-
 3
3
-


WHMCS Import question
in Support
Posted
Well, I guess that is possible modify the WHMCS importer in order to map the services to cPanel Extended instead of cPanel core.